How Does Blockchain Support Data Privacy?
Table of Contents
In recent years, the abrupt increase in security breaches and digital surveillance has highlighted the need for improved privacy and security, particularly regarding users’ data.
Blockchain and distributed ledger provide unseen opportunities for user data protection through decentralized identity and other privacy mechanisms.
Such systems can allow us greater sovereignty with tools enabling them to own and control their data. AI provides further possibilities for enhancing system and user security, enriching data sets, and supporting improved analytical models. Before breaking down the contribution of blockchain to data privacy, let’s take a brief look at blockchain's primary purpose.
What is Blockchain?
Blockchain, introduced in 2008, was defined as a shared, immutable ledger that facilitates recording transactions and tracking assets. Users can see the record of transactions in real-time using a blockchain network.
After fifteen years, online data privacy is a significant concern. More than 80% of users express their thoughts on potential risks from tech giants collecting their data. These tech companies have access to a wide range of personal data about their users, who interact with their websites, buy products, or even search for them. In comparison, some companies are notorious for selling their user's information.

The need for data privacy over the internet is rapidly growing. Because of this decentralized nature, focusing on security is paving the way for ensuring data privacy. Widespread adoptions of Blockchain technology improve users’ personal information, and its ownership is being advocated all around. Blockchain can potentially modify the procedure of gathering information, storing it, and accessing it on the internet while ensuring it is well protected.
You May Also Like | List of Top Tools and Frameworks for Ethereum Development
The Need for Data Privacy
Data privacy is about handling sensitive information, like personal data, securely. It ensures that data is appropriately managed at each stage.
Companies rely on data to analyze essential metrics and grow their businesses. To maintain data privacy, companies must:
- Meet legal responsibilities for collecting, storing, and processing personal data.
- Comply with specific legislation to ensure data privacy in the blockchain.
- Identify stakeholders responsible for rights, liability, and accountability.
Regulating data privacy is easier in private blockchains, which are less complex and don't have a central authority. However, it is more challenging in public blockchains without a governing authority.
If a system with no personal data was involved, would there still be a need for privacy?
The answer is yes. In the 21st century, centralized platforms often need help to protect data privacy effectively. Blockchain technology aims to address this issue with its revolutionary approach. This article explores recent trends and effective ways to handle blockchain security issues.
Let’s take a closer look at how blockchain supports data privacy.
How Does Blockchain Support Data Privacy
Blockchain security solutions offer significant benefits by enabling organizations to share data in new ways, fostering collaboration, operational efficiency, and revenue expansion. However, ensuring data privacy becomes critical in these environments since the data is stored in shared ledgers accessible to multiple participants. According to a blockchain security company, privacy is not inherent to any blockchain itself but can be implemented through layers of privacy.
It is probable for a blockchain security engineer to face the challenge of determining which parties can access and modify transactions and how trades are communicated, validated, and stored. Additionally, updating and enforcing permissions and security measures are crucial considerations. Decisions regarding data ownership and how organizations use data further complicates blockchain privacy decisions.
While blockchain solutions offer valuable opportunities for data sharing and collaboration, maintaining data privacy requires careful consideration of transaction access, communication protocols, and security measures. Ownership and usage rights also contribute to the complexity of privacy discussions in blockchain environments.
Suggested Read | Navigating The Risks of Safe Investment in Blockchain
Decentralized Identity
Decentralized identity (DID) is an interactive blockchain-based concept that empowers individuals with self-sovereign identity, enhancing the privacy and security of personal data on a blockchain database. DID allows individuals to take ownership of their digital identity across various aspects. Microsoft, involved in defining DID standards, emphasizes the need to regain control over our identity and digital interactions owned and controlled by third parties without our knowledge.
Creating a DID is open to anyone; initially, it contains no attached information. Users can associate identifying data, such as a driver's license, with their DID as time passes. Verifying ownership of a DID is similar to validating email ownership. For instance, a private message with a security code can be sent to an email address associated with an online gaming account, ensuring that only the person with access to the email's password can provide the code.
Unlike an email account, a DID is owned and stored by the individual, and the owner securely holds the private key (password). Personal information related to the identity can be stored in an identity hub—a secure, encrypted repository outside the blockchain, potentially spread across devices like phones, PCs, cloud storage, or offline storage devices. With an identity hub, individuals control which information they share with external parties.
DIDs effectively mitigate the risk of unwanted correlation. Using standard identifiers across multiple websites, like email addresses, can lead to correlation issues. Correlation refers to unauthorized associations between a user's identity information across various systems. When users provide the same email address on different sites and additional personal details, they unknowingly enable the potential for correlation. Entities can then link and correlate data from other locations, potentially compromising privacy tokens in blockchain.
DIDs offer an interactive solution to empower individuals with self-sovereign identities. By regaining control over personal data and utilizing identity hubs, individuals can selectively share information while reducing the risk of unwanted correlation across multiple systems.

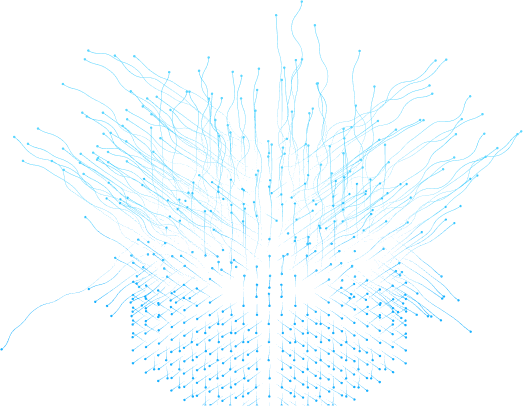
Tracking cookies and web clicks have the potential to link user identities across different websites, allowing outsiders to gather extensive information such as location, gender, age range, interests, and more. The above figure illustrates how users can store their data in a centralized location under their control and interact separately with each service provider. This approach allows users to control which specific pieces of information are visible to each provider.
Federated identity
Blockchains offer a way to safeguard individuals' privacy, essential for self-sovereign identity. Traditionally, users rely on a federated identity, which is used to access blockchain security services by multiple parties through a single sign-on (SSO) authentication. For instance, a single sign-on credential or digital federated identity grants access to all services in a healthcare network with hospitals, insurance carriers, and urgent care clinics.
However, this type of identity, usually stored and managed centrally by a service provider, is susceptible to security vulnerabilities. Blockchain for data security establishes more secure and federated identities with single sign-on capabilities. There is a framework called blockchain-based federated identity (BFID), where the network of providers manages the system, identification, and authentication of users instead of a centralized third party.

In a BFID, any entity within the blockchain network can verify credentials and issue user identities. All transactions are recorded and maintained on the blockchain, leveraging its secure and immutable nature. This approach significantly reduces the risk of identity breaches and potential theft, as the distributed ledger prevents unauthorized tampering.
Blockchain offers a more secure approach to federated identities using a blockchain-based framework. With decentralized management and the immutability of the blockchain, identity breaches, and theft can be practically eliminated, ensuring enhanced privacy protection and the future of blockchain technology.
Zero-Knowledge Proofs
Zero-knowledge proofs use cryptographic techniques to demonstrate the truth of a statement without revealing any actual data. Let's say the government issues a driver's license for people over 21 years old. During the license application process, they ask the driver to input a secret nickname that only they know. This nickname gets combined with their license number and stored in a public list of valid drivers over 21.
Now, imagine you go to a bar and want to prove that you're of legal age without showing your actual ID. You can enter your nickname and license number into a special tool that generates a unique code called a hash. If the resulting hash matches any code on the public list, the bartender can confirm that you are indeed old enough to enter.
There are two types of zero-knowledge proofs:
Interactive
non-interactive
The most common type is interactive, where the person or a computer (the prover) and the verifier engage in a series of questions or challenges. By answering these correctly a certain number of times, the prover can convince the verifier with high confidence that their statement is true.
Let's take another example of an interactive zero-knowledge proof using two identical balls, one red, and one blue. In this scenario, the verifier is color-blind and cannot tell the colors of the balls. Your objective as the prover is to prove to the verifier that the balls are indeed different colors.

The verifier takes the balls behind their back and reveals one of the balls without disclosing its color. As the prover, you indicate the color you believe it to be. The verifier repeats this process and asks if they switched the ball between the rounds.
Since you can see the different colors of the balls, you can confidently determine whether or not the ball was switched. Through multiple rounds of this interaction, the probability of you guessing correctly every time decreases significantly. This increasing level of statistical certainty indicates that there are indeed two different-colored balls.
Zero-knowledge proofs are valuable tools for security and privacy on blockchain for maintaining control over personal information. They enable individuals to provide the information required while revealing the least amount of additional details. Such blockchain privacy solutions ensure property control, allowing individuals to protect their sensitive information effectively.
Use Cases of Blockchain in Data Privacy
Here are some examples of how blockchain technology is used to enhance blockchain and data privacy in various domains:
Healthcare Records: By storing medical data on the blockchain, patients have control over who can access their records, enabling secure sharing among healthcare providers while maintaining privacy blockchain projects.
Identity Verification: Blockchain provides a decentralized and secure solution for identity verification. Users can share specific identity attributes without revealing their personal information, ensuring privacy on blockchain platforms.
Supply Chain Management: Blockchain enables tracking and verification of every step in the supply chain, ensuring authenticity and preventing unauthorized access or tampering. It protects sensitive information and trade secrets.
Financial Transactions: Blockchain technology in cryptocurrencies facilitates secure and private financial transactions. Users can transfer funds directly without intermediaries, reducing the risk of fraud and ensuring privacy.
IoT Data Security: Blockchain security ensures the privacy of data generated by Internet of Things (IoT) devices. It enables secure communication and data exchange, encrypted storage, and protection against unauthorized access.
Voting Systems: Blockchain data security can revolutionize voting systems by providing secure and transparent elections. It ensures privacy for voters while maintaining the integrity of the voting process, recording each vote securely on the blockchain.
These use cases demonstrate how blockchain technology can enhance blockchain privacy protection in various industries, providing individuals with greater control over their information and reducing the risk of unauthorized access or tampering.
Also, Visit | Building Blocks of Empowered Blockchain Scalability Solutions
Conclusion
Blockchain and AI technologies are evolving rapidly, opening up new possibilities for data sharing and integration that were previously unimaginable. These advancements also bring about opportunities for the ethical use of data. However, the sharing of personal data poses a dilemma for both individuals and organizations, as it can offer valuable benefits but also entail significant risks and costs.
Fortunately, blockchain introduces innovative mechanisms like decentralized identities and zero-knowledge proofs, which enable data to be shared while preserving individual privacy and granting users control over their data. These technological advancements not only enhance cybersecurity but also promote the ethical utilization of personal data.
To achieve these desirable outcomes, participants in the blockchain ecosystem need to develop and implement effective governance frameworks and mechanisms. By doing so, they can ensure that data-sharing practices align with privacy principles, empowering individuals to maintain ownership and control over their personal information while enabling responsible and ethical use by organizations.
Table of Contents
In recent years, the abrupt increase in security breaches and digital surveillance has highlighted the need for improved privacy and security, particularly regarding users’ data.
Blockchain and distributed ledger provide unseen opportunities for user data protection through decentralized identity and other privacy mechanisms.
Such systems can allow us greater sovereignty with tools enabling them to own and control their data. AI provides further possibilities for enhancing system and user security, enriching data sets, and supporting improved analytical models. Before breaking down the contribution of blockchain to data privacy, let’s take a brief look at blockchain's primary purpose.
What is Blockchain?
Blockchain, introduced in 2008, was defined as a shared, immutable ledger that facilitates recording transactions and tracking assets. Users can see the record of transactions in real-time using a blockchain network.
After fifteen years, online data privacy is a significant concern. More than 80% of users express their thoughts on potential risks from tech giants collecting their data. These tech companies have access to a wide range of personal data about their users, who interact with their websites, buy products, or even search for them. In comparison, some companies are notorious for selling their user's information.

The need for data privacy over the internet is rapidly growing. Because of this decentralized nature, focusing on security is paving the way for ensuring data privacy. Widespread adoptions of Blockchain technology improve users’ personal information, and its ownership is being advocated all around. Blockchain can potentially modify the procedure of gathering information, storing it, and accessing it on the internet while ensuring it is well protected.
You May Also Like | List of Top Tools and Frameworks for Ethereum Development
The Need for Data Privacy
Data privacy is about handling sensitive information, like personal data, securely. It ensures that data is appropriately managed at each stage.
Companies rely on data to analyze essential metrics and grow their businesses. To maintain data privacy, companies must:
- Meet legal responsibilities for collecting, storing, and processing personal data.
- Comply with specific legislation to ensure data privacy in the blockchain.
- Identify stakeholders responsible for rights, liability, and accountability.
Regulating data privacy is easier in private blockchains, which are less complex and don't have a central authority. However, it is more challenging in public blockchains without a governing authority.
If a system with no personal data was involved, would there still be a need for privacy?
The answer is yes. In the 21st century, centralized platforms often need help to protect data privacy effectively. Blockchain technology aims to address this issue with its revolutionary approach. This article explores recent trends and effective ways to handle blockchain security issues.
Let’s take a closer look at how blockchain supports data privacy.
How Does Blockchain Support Data Privacy
Blockchain security solutions offer significant benefits by enabling organizations to share data in new ways, fostering collaboration, operational efficiency, and revenue expansion. However, ensuring data privacy becomes critical in these environments since the data is stored in shared ledgers accessible to multiple participants. According to a blockchain security company, privacy is not inherent to any blockchain itself but can be implemented through layers of privacy.
It is probable for a blockchain security engineer to face the challenge of determining which parties can access and modify transactions and how trades are communicated, validated, and stored. Additionally, updating and enforcing permissions and security measures are crucial considerations. Decisions regarding data ownership and how organizations use data further complicates blockchain privacy decisions.
While blockchain solutions offer valuable opportunities for data sharing and collaboration, maintaining data privacy requires careful consideration of transaction access, communication protocols, and security measures. Ownership and usage rights also contribute to the complexity of privacy discussions in blockchain environments.
Suggested Read | Navigating The Risks of Safe Investment in Blockchain
Decentralized Identity
Decentralized identity (DID) is an interactive blockchain-based concept that empowers individuals with self-sovereign identity, enhancing the privacy and security of personal data on a blockchain database. DID allows individuals to take ownership of their digital identity across various aspects. Microsoft, involved in defining DID standards, emphasizes the need to regain control over our identity and digital interactions owned and controlled by third parties without our knowledge.
Creating a DID is open to anyone; initially, it contains no attached information. Users can associate identifying data, such as a driver's license, with their DID as time passes. Verifying ownership of a DID is similar to validating email ownership. For instance, a private message with a security code can be sent to an email address associated with an online gaming account, ensuring that only the person with access to the email's password can provide the code.
Unlike an email account, a DID is owned and stored by the individual, and the owner securely holds the private key (password). Personal information related to the identity can be stored in an identity hub—a secure, encrypted repository outside the blockchain, potentially spread across devices like phones, PCs, cloud storage, or offline storage devices. With an identity hub, individuals control which information they share with external parties.
DIDs effectively mitigate the risk of unwanted correlation. Using standard identifiers across multiple websites, like email addresses, can lead to correlation issues. Correlation refers to unauthorized associations between a user's identity information across various systems. When users provide the same email address on different sites and additional personal details, they unknowingly enable the potential for correlation. Entities can then link and correlate data from other locations, potentially compromising privacy tokens in blockchain.
DIDs offer an interactive solution to empower individuals with self-sovereign identities. By regaining control over personal data and utilizing identity hubs, individuals can selectively share information while reducing the risk of unwanted correlation across multiple systems.

Tracking cookies and web clicks have the potential to link user identities across different websites, allowing outsiders to gather extensive information such as location, gender, age range, interests, and more. The above figure illustrates how users can store their data in a centralized location under their control and interact separately with each service provider. This approach allows users to control which specific pieces of information are visible to each provider.
Federated identity
Blockchains offer a way to safeguard individuals' privacy, essential for self-sovereign identity. Traditionally, users rely on a federated identity, which is used to access blockchain security services by multiple parties through a single sign-on (SSO) authentication. For instance, a single sign-on credential or digital federated identity grants access to all services in a healthcare network with hospitals, insurance carriers, and urgent care clinics.
However, this type of identity, usually stored and managed centrally by a service provider, is susceptible to security vulnerabilities. Blockchain for data security establishes more secure and federated identities with single sign-on capabilities. There is a framework called blockchain-based federated identity (BFID), where the network of providers manages the system, identification, and authentication of users instead of a centralized third party.

In a BFID, any entity within the blockchain network can verify credentials and issue user identities. All transactions are recorded and maintained on the blockchain, leveraging its secure and immutable nature. This approach significantly reduces the risk of identity breaches and potential theft, as the distributed ledger prevents unauthorized tampering.
Blockchain offers a more secure approach to federated identities using a blockchain-based framework. With decentralized management and the immutability of the blockchain, identity breaches, and theft can be practically eliminated, ensuring enhanced privacy protection and the future of blockchain technology.
Zero-Knowledge Proofs
Zero-knowledge proofs use cryptographic techniques to demonstrate the truth of a statement without revealing any actual data. Let's say the government issues a driver's license for people over 21 years old. During the license application process, they ask the driver to input a secret nickname that only they know. This nickname gets combined with their license number and stored in a public list of valid drivers over 21.
Now, imagine you go to a bar and want to prove that you're of legal age without showing your actual ID. You can enter your nickname and license number into a special tool that generates a unique code called a hash. If the resulting hash matches any code on the public list, the bartender can confirm that you are indeed old enough to enter.
There are two types of zero-knowledge proofs:
Interactive
non-interactive
The most common type is interactive, where the person or a computer (the prover) and the verifier engage in a series of questions or challenges. By answering these correctly a certain number of times, the prover can convince the verifier with high confidence that their statement is true.
Let's take another example of an interactive zero-knowledge proof using two identical balls, one red, and one blue. In this scenario, the verifier is color-blind and cannot tell the colors of the balls. Your objective as the prover is to prove to the verifier that the balls are indeed different colors.

The verifier takes the balls behind their back and reveals one of the balls without disclosing its color. As the prover, you indicate the color you believe it to be. The verifier repeats this process and asks if they switched the ball between the rounds.
Since you can see the different colors of the balls, you can confidently determine whether or not the ball was switched. Through multiple rounds of this interaction, the probability of you guessing correctly every time decreases significantly. This increasing level of statistical certainty indicates that there are indeed two different-colored balls.
Zero-knowledge proofs are valuable tools for security and privacy on blockchain for maintaining control over personal information. They enable individuals to provide the information required while revealing the least amount of additional details. Such blockchain privacy solutions ensure property control, allowing individuals to protect their sensitive information effectively.
Use Cases of Blockchain in Data Privacy
Here are some examples of how blockchain technology is used to enhance blockchain and data privacy in various domains:
Healthcare Records: By storing medical data on the blockchain, patients have control over who can access their records, enabling secure sharing among healthcare providers while maintaining privacy blockchain projects.
Identity Verification: Blockchain provides a decentralized and secure solution for identity verification. Users can share specific identity attributes without revealing their personal information, ensuring privacy on blockchain platforms.
Supply Chain Management: Blockchain enables tracking and verification of every step in the supply chain, ensuring authenticity and preventing unauthorized access or tampering. It protects sensitive information and trade secrets.
Financial Transactions: Blockchain technology in cryptocurrencies facilitates secure and private financial transactions. Users can transfer funds directly without intermediaries, reducing the risk of fraud and ensuring privacy.
IoT Data Security: Blockchain security ensures the privacy of data generated by Internet of Things (IoT) devices. It enables secure communication and data exchange, encrypted storage, and protection against unauthorized access.
Voting Systems: Blockchain data security can revolutionize voting systems by providing secure and transparent elections. It ensures privacy for voters while maintaining the integrity of the voting process, recording each vote securely on the blockchain.
These use cases demonstrate how blockchain technology can enhance blockchain privacy protection in various industries, providing individuals with greater control over their information and reducing the risk of unauthorized access or tampering.
Also, Visit | Building Blocks of Empowered Blockchain Scalability Solutions
Conclusion
Blockchain and AI technologies are evolving rapidly, opening up new possibilities for data sharing and integration that were previously unimaginable. These advancements also bring about opportunities for the ethical use of data. However, the sharing of personal data poses a dilemma for both individuals and organizations, as it can offer valuable benefits but also entail significant risks and costs.
Fortunately, blockchain introduces innovative mechanisms like decentralized identities and zero-knowledge proofs, which enable data to be shared while preserving individual privacy and granting users control over their data. These technological advancements not only enhance cybersecurity but also promote the ethical utilization of personal data.
To achieve these desirable outcomes, participants in the blockchain ecosystem need to develop and implement effective governance frameworks and mechanisms. By doing so, they can ensure that data-sharing practices align with privacy principles, empowering individuals to maintain ownership and control over their personal information while enabling responsible and ethical use by organizations.
FAQS
Blockchain provides confidentiality through the use of cryptographic techniques. Each transaction or data entry is encrypted; only those with the corresponding private keys can access and decipher the information. Additionally, blockchain's decentralized nature ensures that no single entity has complete control over the data, reducing the risk of unauthorized access or manipulation.
Blockchain differs from a regular database in three key ways. Firstly, it is decentralized, eliminating the need for a central authority. Secondly, blockchain data is immutable and tamper-proof, ensuring the integrity of the stored information. Lastly, blockchain provides transparency and trust among participants, as all transactions are visible to the network, unlike regular databases that often rely on faith in a central authority.
Blockchain is difficult to hack due to its robust security measures. The decentralized nature of blockchain means there is no central point of vulnerability for attackers to exploit. Instead, the network consists of multiple nodes, and a hacker would need to gain control over most of these nodes simultaneously, which could be more practical. Additionally, blockchain employs advanced cryptographic techniques, such as hashing and digital signatures, which complicate altering or tampering with data without detection.
No, someone cannot steal your cryptocurrency with just your wallet address. The wallet address is a public key used for receiving funds and does not contain sensitive information like private keys. To steal your cryptocurrency, an attacker would need access to your private keys or mnemonic phrase, which should be kept secure and not shared with anyone.
Java and Python can be used for blockchain development, and the choice depends on various factors. Java is known for its performance and is commonly used in enterprise blockchain solutions. On the other hand, Python offers simplicity and ease of use, making it suitable for rapid prototyping and development.
Yes, blockchain development typically requires coding. Building and implementing blockchain solutions involve creating intelligent contracts, writing code for decentralized applications (DApps), developing consensus algorithms, and interacting with blockchain networks through APIs or SDKs. Proficiency in programming languages like Solidity (for Ethereum), JavaScript, Python, or Go is often necessary to work with blockchain technologies effectively.